- PLN: The significance of PLN for good interaction in social media environments because PLNs can help people communicate and collaborate together on the Web. There is a great need for such technology to operate on the Internet, and it is beneficial to help people build relationships and expand their knowledge base. In addition, it can change the way people connect on the Internet. Our team thought of this when considering the topic. Weibo, as a social platform, can not only build social connections but also expand knowledge. And Weibo is available in most countries, as well as international versions. This allows people to communicate and connect together in any country, in different time zones.
- The digital age: The digital age is based on information technology networks, which can edit many things into electronic signal streams and binary them for processing. For example, sampling, encoding, sound, pictures, and so on. At the same time, it has changed the way of life of people in today’s society. For example, games, entertainment, shopping, information trading, and so on. These online lifestyles have greatly improved and enhanced people’s quality of life. Until now, technology has become more advanced and advances, in VR have improved medical technology. This is because VR allows for human-machine interaction, environmental stimulation, and doing simulated surgery. This virtual world can have many implications for people. People will spend a lot of energy and time studying this technology. In this research, people can put their visions and wishes for the future in the virtual world. Satisfy their inner world. But the digital age also has its drawbacks, such as digital privacy.
- Digital privacy: Digital privacy for the protection of information about citizens who use digital media. If once digital privacy is compromised, the personal privacy of this city is also compromised. Therefore, in the age of digital information, many people are concerned about the security of their personal data. If there is no way to safeguard the privacy of the public, users will not choose to use this software. But even though most software and websites promise not to contain leakage of user privacy, it is still not safe. The fact is that using digital media for matters, whether personal or online, leaves a digital footprint. Digital privacy can also be extended to the use of domain names. This is a way to help web users protect their personal information. We use real names in our recommended Weibo, so there is a greater possibility of privacy leaks. But you can avoid online disinformation.
- Education Model: Different education styles and educational philosophies will bring up children with different personalities, perspectives, and ideas. For different countries, talent training and selection paths are different and have a great impact on the ideology and overall social perception of the nation. A big reason for this is that the education models are not the same. The advantages of the traditional education model are the low economic cost, the reduction of complicated work such as making courseware, and the simplicity and convenience. However, it has the disadvantage of being too boring and more suitable for examinations. It is not conducive to broadening the horizons and expanding the knowledge of teachers and students. The advantage of modern technology is that it avoids the disadvantages of traditional education and uses modern technology to bring advanced content and a wealth of knowledge to students. At the same time, what they have in common is that they are all about student progress, and schools can use both mo s simultaneously
- Plagiarism checker: Plagiarism checker is a technology that every student knows about because school papers need to be tested for plagiarism or similarity. The invention of this technology has reduced plagiarism. And this technology is supported by many people, and it really brings a lot of convenience in the actual use process. If the repetition rate is high, students can revise it in time. In addition, the detection system is more secure, which can effectively guarantee the security. Choosing a detection system with high security not only allows you to test your paper but also prevents personal information or the content of your paper from being leaked. The detection system is also more efficient. The general website has a word limit, so the slowest a few minutes can be detected. Comparative results and testing reports are available in a short time. This is much better efficiency for students to revise their papers.
- Team work conclution: The Weibo platform is relatively accessible and inclusive. web accessibility is relatively good for different people to access. This viewpoint is also of greater concern to our team. Our team works in a process of division of labor, where everyone makes a plan and then assigns it. Everyone chooses their own strengths to complete the content. This largely refines and improves the quality of our work. In addition, We chose Weibo as a platform because our group members all use it and are very good at it. For its advantages and disadvantages, we can also find it very well. Therefore, we can find the information we need better and faster. The need for teamwork is shared commitment. This shared commitment needs to have its own content, be challenging, and be agreed upon by everyone. For me, I am personally very happy with our team. We had discussions before and respected each other. When we have a problem, we solve it together.
Author: pudding34
✔️ Digital Identity How do you present yourself in social media? Do you have separate identities for personal and work or school use? Do you integrate your personal and professional identities? Do you use different platforms for different purposes?
Personally, I rarely post content on social media platforms, but I use social media regularly to read news, such as various news, learning content, funny videos, and so on. I generally have only one account per platform because I do not post content, so I do not need to use it separately. I use different platforms for a number of reasons, the first point is that the content of different platforms is different, the second point is to follow the trend, and the third point is to understand the media information.
✔️ Access and Inclusion How does the platform you chose for the Major Project incorporate accessibility and inclusion principles. How are disabled people treated on the platform? Are there multiple ways people can consume or produce content to meet accessibility needs? How do you include those who might otherwise be excluded?
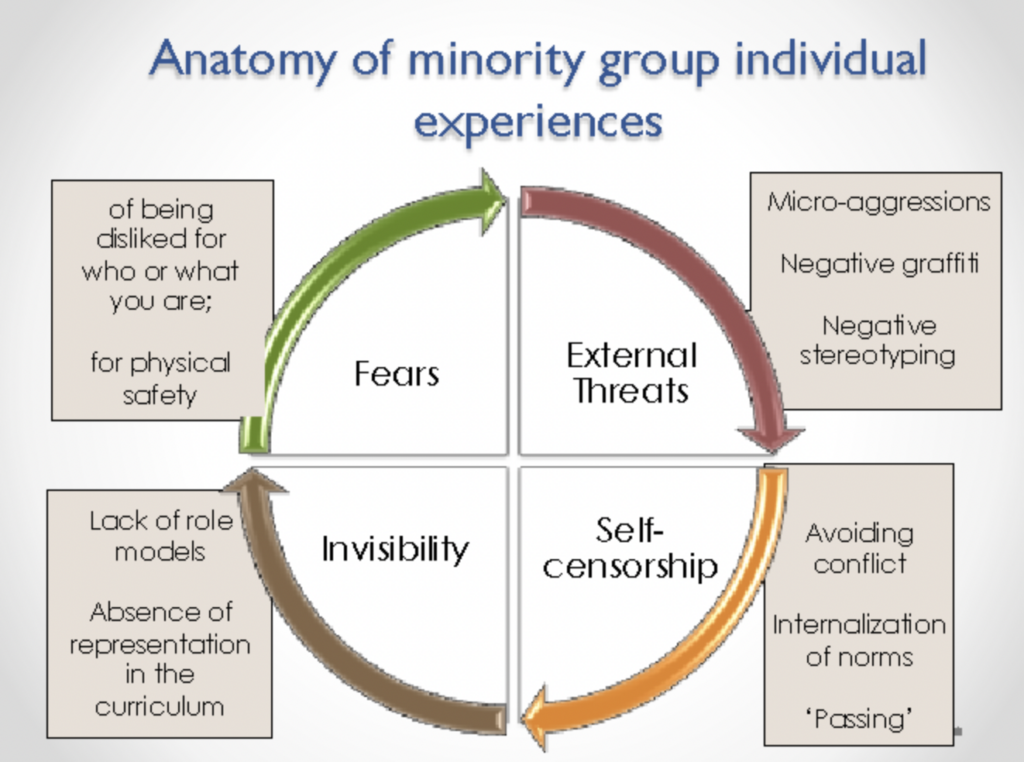
There is no difference between anonymous disabled people on social platforms and ordinary people. Everyone is just an ordinary user. However, disabled bloggers on social media platforms are more likely to get attention. Web accessibility means making the same information accessible to everyone, regardless of their disabilities, user have to access Web content through user agents. Therefore accessibility has to be improved. At the Internet becomes a major source of enteratinment, communication, and e-commerce, it is possible for people to satisfy these needs through content or consumption. Nevertheless, most websites remain inaccessible to people with disabilities because they are not designed with their needs in mind. however, it is possible to ctegorize disabilities, so that they can be used by people with disabilities without any hindrance.
✔️ Media Literacy, Trust, and Disinformation Does your chosen platform have content moderation policies? Does it flag disinformation, or provide links to trusted resources? How do you ensure that you don’t spread disinformation as misinformation?
Weibo has a content review policy and flags false information. Since the main audience of Weibo is Chinese, China will be more strict in terms of politics. Therefore, sensitive information is handled and false information is minimized. Weibo is a platform with many official accounts and cyber police. Once it is determined to be false information, it will soon be reported, blocked, and clarified. Therefore, netizens will soon realize that it is false information and also reduce the spread.
A plagiarism checker is mainly used to detect whether plagiarism. For example, teachers like to use this software to detect whether their students’ papers are plagiarized or not. But this type of technology also seems to be used in economic terms.
Wow:
- Plagiarism checker can effectively help teachers check plagiarism.
- Identidy at-risk students and develop remediation plans.
- Promising one-stop store for a variety of technology-driven instructional services.
Wonders:
I wonder how far and how effective can be the development of such plagiarism checkers be?

Related Course Links:
As social networks and news media grow faster and faster, false information is spreading rapidly on the Internet. Since many people post information anonymously on social media, this leads them not to carefully confirm the accuracy of the information. This can have a very bad effect on society.
Wow:
- The rapid development of social media has led to a variety of ways for people to socialize.
- But anonymity leads to people talking out of turn on the Internet. Fake new is becoming more and more common.
- At the same time, amplified propaganda seriously endangers the social order.
Wonder:
I wonder if removing anonymity makes fake messages lee frequent? But would this result in no one daring to post real information in their real names? Such as fear of retaliation.

Related Course Links:

The concept of digital privacy can be described as the protection of information about citizens who use digital media, such as some social media and websites, which are digital media. Digital privacy is equivalent to the personal privacy of citizens on the Internet. In the age of digital information, many people are most concerned and worried about the security of their personal data. However, in the current network environment, the protection of personal privacy is not perfect, and there are even big loopholes. In fact, using unfamiliar Wi-Fi outdoor for work or entertainment can leave a digital trail on the network. Such traces can lead to personal privacy leaks and such vulnerabilities can easily be used by some people to do bad things.
Although, cyber security experts strive to help computer users protect personal information. But hacking techniques are also advancing and it is difficult to go for very tight protection. Even now, many cell phone software is forcibly collecting the personal information of users. This has led to a distrust of the Internet by many citizens. The debate over digital privacy is slowly diminishing as technology advances. The reason for this is that some users believe in advanced technology and the company’s commitment. A very large percentage of users also do so because there is no way to leave the network and they are forced to accept and trust that their privacy will not be compromised. At the same time, many users on the Internet are not aware of the need to protect their digital information awareness.
With the development of mobile Internet including 5G technology, it is absolute that people’s information is leaked. Therefore, we must first be prepared for this idea. Internet data development is getting better and better, and the means of collecting, organizing, analyzing, and predicting user data in information system services are getting more and more mature. For example, a woman often searches for information about cosmetics, and her phone will often push cosmetics ads to her. Also if one type of video is often watched on TikTok, it will push related videos to the user. This situation is a disguised leakage of personal information. But most users choose to accept it because it improves their online experience. In the face of such a situation, first of all, the protection of digital data must be continuously improved. And secondly, the relevant laws must be improved. Finally, citizens should also be aware of self-prevention and not disclose privacy on their own.
To conclude, in the face of the online environment, users must protect their personal privacy. When users find out that their personal privacy has been compromised, the user must use the law to protect themselves.
Related Course Link and Materials:
First Comment:
I think Jiaxin’s point of view is very similar to mine, and she found some problems that I did find. For example, she believes that users can use the Internet to build good social relationships with others and to communicate about their studies and work, all of which are beneficial to the development and convenience of users in all aspects. However, I am more answering the question of data privacy for users. So all in all, we both found different focuses in our articles, but the direction of thinking is the same.
Second Comment:
Jingjing’s article shows that technology is evolving faster and faster, and that the advantages outweigh the disadvantages, such as the unity of continuity for residents and visitors. I think that is a good point and even gives me a good idea. Then, the questions in her wonder were the ones I focused on answering in my showcase.
Each country has a different educational model, which reflects the diversity of education. For example, traditional education models and modern technology education. Both models have advantages and disadvantages, but what they have in common is that they are all about the betterment of students.
Wow:
- Education is not only about imparting knowledge, but also about developing students’ strengths.
- Modern technology education can enhance the personalized educational environment, which requires strong technical support.
- The traditional education model can be relatively conservative and srict and stereotypicl.
Wonder:
I wonder if the fact that big cities are using technology in education means that the traditional education model is obsolete.
Related Course Links:
https://ebookcentral-proquest-com.ezproxy.library.uvic.ca/lib/uvic/reader.action?docID=4832579&ppg=6
In the era of digital information, the most important concern and worry for many people is whether personal data security is safe. In the whole global network environment, the privacy of the masses is hardly guaranteed, and even the country’s network is not necessarily secure. In this situation, privacy leakage will lead to more and more fraudulent behavior, which will also lead to companies will lose a lot of customers. Although many technical departments are perfecting this technology now.
Wow:
- Internet data is developing better and better, and the means of collecting, organizing, analyzing and predicting user data in information system services are maturing.
- If hackers get hold of the data, it is easy to cause a privacy breach.
- At prsent, the major platforms are relatively simple means of authentication, behind which hides a greter risk of leakage of personal privacy information.
Wonder:
I think it is not the best done yet. I wonder if there is any better way to change this situation?
Related Course Links:
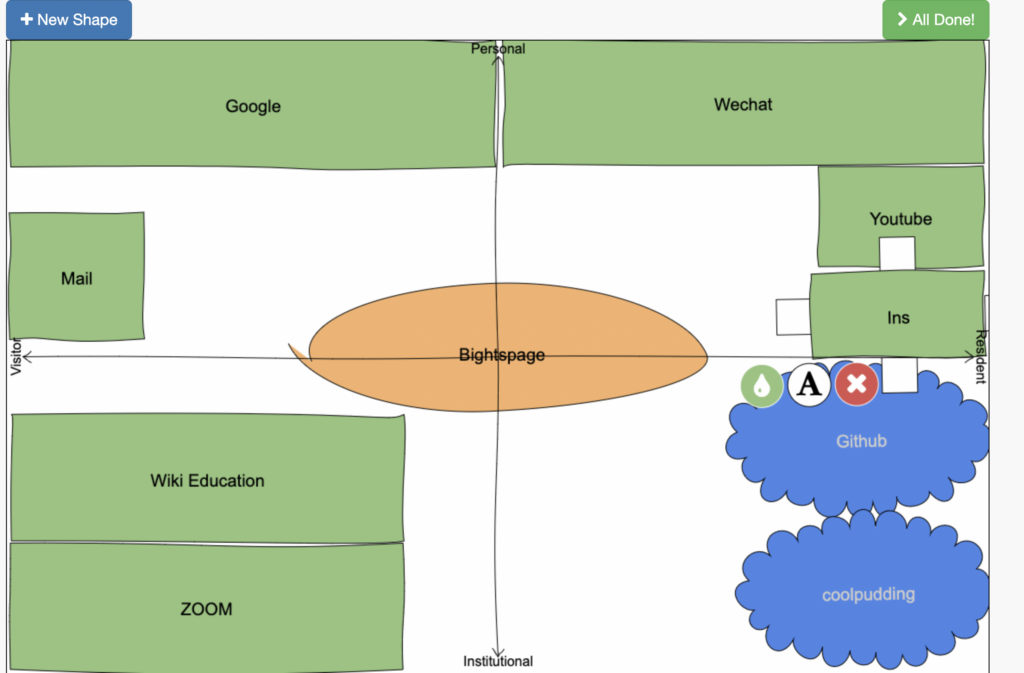
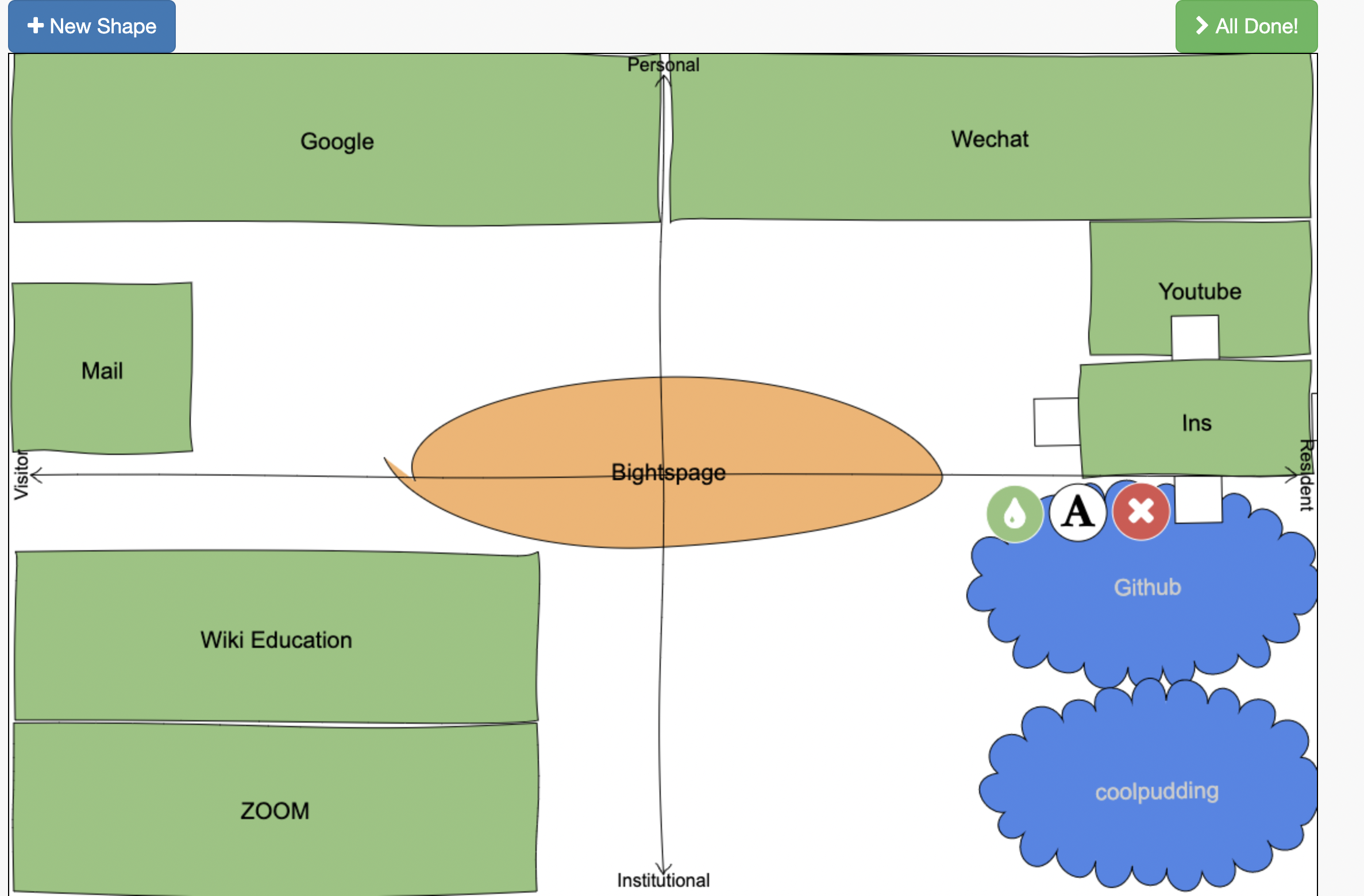
https://cmadland.github.io/edci338-202201/articles.html#visitors-and-residents-a-new-typology-for-online-engagement
My own Visitor/Resident map:
The digital age is the age of technology, mainly used in electronic devices. For example, cell phones, computers, and other electronic devices. In modern society, people rely heavily on electronic devices, which indirectly indicates a greater reliance on electromagnetic energy. The development of technology has gradually changed people’s way of life, and the power of the Internet has led to people being able to do many things without having to face each other.
PLN can help people to communicate and collaborate together on the web, and it is much like social media in nature, mainly in that it helps people to build relationships and expand their knowledge base. At the same time, it can even change the way people connect with each other, which allows them to solve the problem of whether they are in the same place or not. They can communicate and learn together in any country, time zone. It is even possible to solve many computer problems remotely.
Recent Comments